| Sunday, December 25, 2005 |
| ECHELON |
On Joe's desk sits a Gateway personal computer with a 1.6 GHz Pentium 4 processor with 384 MB of RAM, internal storage of 127 GB and an external hard drive with 160 GB of free space. The system is capable of processing 3.2 GB of data per second. Today, you could pick up a similar system on eBay for roughly $300. For $39.99 per month, this PC is connected to a 3 Mbps Internet connection capable of downloading a 10-minute video in a matter of seconds. Imagine a supercomputer that a government agency with a budget of $3.6 billion could operate. I'll help: You can't imagine it.
In 1947, the governments of the United States, the United Kingdom, Canada, Australia and New Zealand signed a secret treaty in which they agreed to cooperate in matters of signals intelligence. The government agreed to pool their geographic and technological assets in order to listen in on the electronic communications of China, the Soviet Union and others. In the 1982 book entitled The Puzzle Palace (I've read through it twice), James Bamford describes how he discovered that the allies were developing a system called PLATFORM, which would integrate at least 52 separate SIGINT agency computer systems into one central network run out of Fort Meade, Maryland.
Today, that computer system's name is ECHELON and it is funded in part by the National Security Agency/Central Security Service (NSA/CSS)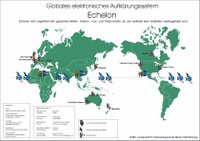 headquartered at Fort Meade. ECHELON functions as a real-time intercept and processing operation geared toward civilian communications. Obviously, the NSA targets military communication with other systems. ECHELON's first component targets international phone company telecommunications satellites (or Intelsats) from a series of five ground intercept stations located at Yakima, Washington; Sugar Grove, West Virginia; Morwenstow in Cornwall, England; Waihopai, New Zealand; and Geraldton, Australia. headquartered at Fort Meade. ECHELON functions as a real-time intercept and processing operation geared toward civilian communications. Obviously, the NSA targets military communication with other systems. ECHELON's first component targets international phone company telecommunications satellites (or Intelsats) from a series of five ground intercept stations located at Yakima, Washington; Sugar Grove, West Virginia; Morwenstow in Cornwall, England; Waihopai, New Zealand; and Geraldton, Australia.
The next component targets other civilian communications satellites; and the final component intercepts international communications -- all components target email, fax and phone transmissions. A list of keywords or phrases are entered by each country into a "Dictionary" computer, which, after recognizing keywords, intercepts full transmissions and forwards them to analysts.
More than 20 years ago, the CIA director told congressional investigators that the NSA monitored every overseas call made from the United States. In 1996, British Telecom accidentally disclosed in a court case that it had provided a station with equipment which could allow it access to hundreds of thousands of European calls a day. Today, I searched Google for the keyword "echelon" and was given 7,760,000 results in 0.11 seconds. A former NSA officer reminds us "people working on the outer edges have capabilities far in excess of what you do.
ECHELON has the capability to intercept millions of communiques per hour. Therefore, there's a real problem sorting and reading all of the data. It's possible that most of the intercepts are sitting stored and unused. I definitely will not lose sleep over it.
But as with all of the powerful assets that are at the United States Government's disposal, there is potential for abuse. And that, ultimately, is what should be at the root of the recent wiretapping accusations -- not the political maneuvering that is currently taking place in Washington. |
posted by Joe Napalm @ 10:09 PM   |
|
|
|
|
|




Is that sarcasm?